Unified Security Management & Threat Intelligence
AlienVault is a company operating in the field of information security since 2007. AlienVault products protect businesses of all sizes against today’s most advanced threats.
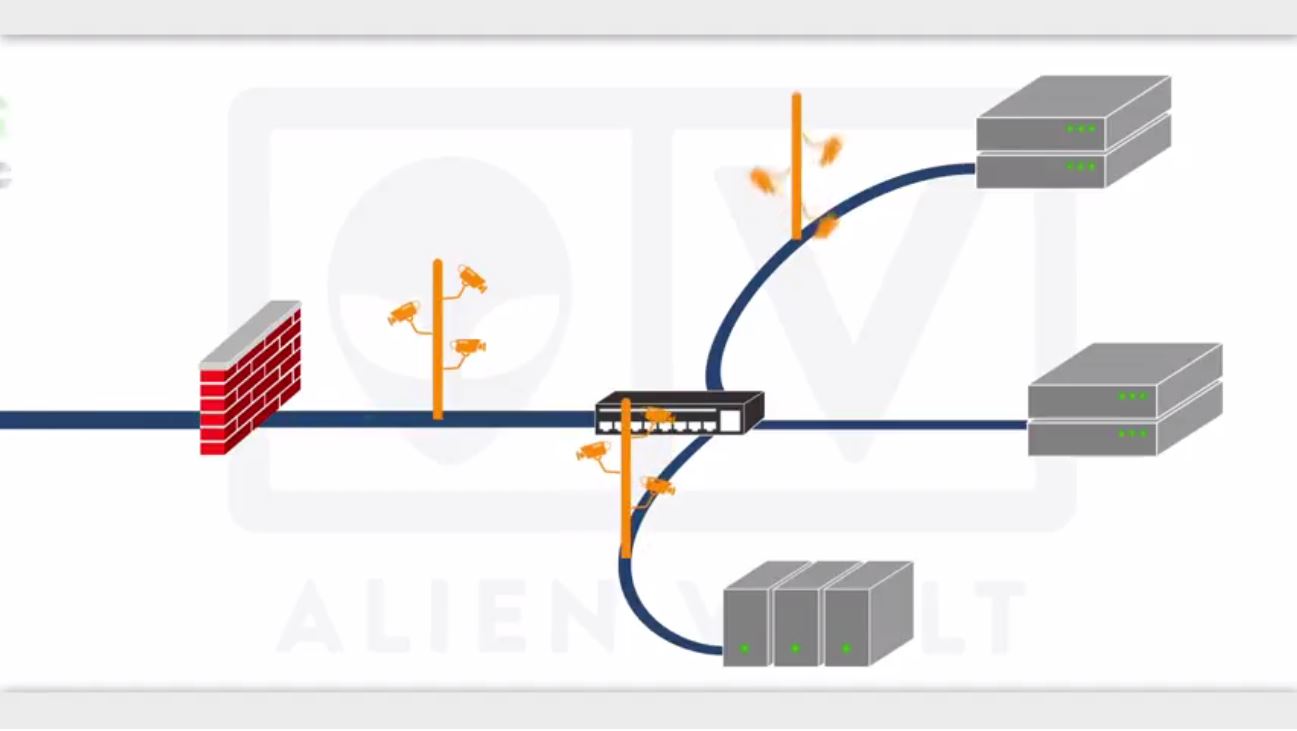
AlienVault Network Security
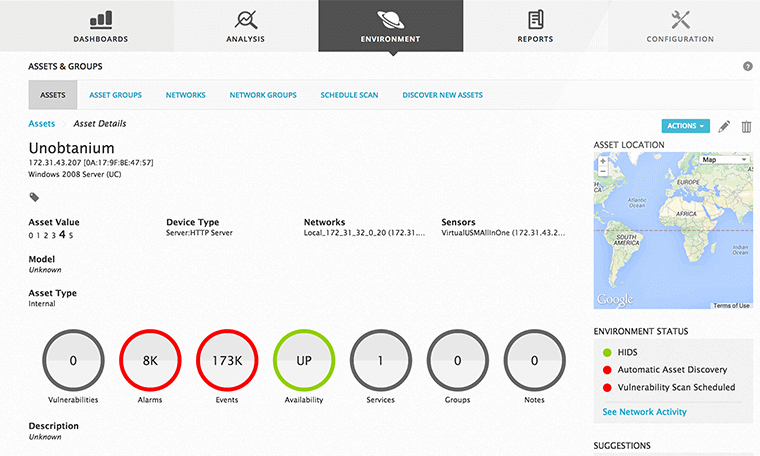
All the mandatory security features you need are possible with the Unified Security Management platform. The fastest and easiest system to fully view the security status of your network and take action against vulnerabilities that threaten information security.
AlienVault Compliance Manager
The secret to success is to simplify key security checks so that they can be performed automatically and regularly, effectively prioritizing remediation efforts and making visibility one. AlienVault Unified Security Management solutions automatically identify important audit activities, providing reports and alerts on those that require urgent action.
AlienVault USM Compliance Benefits:
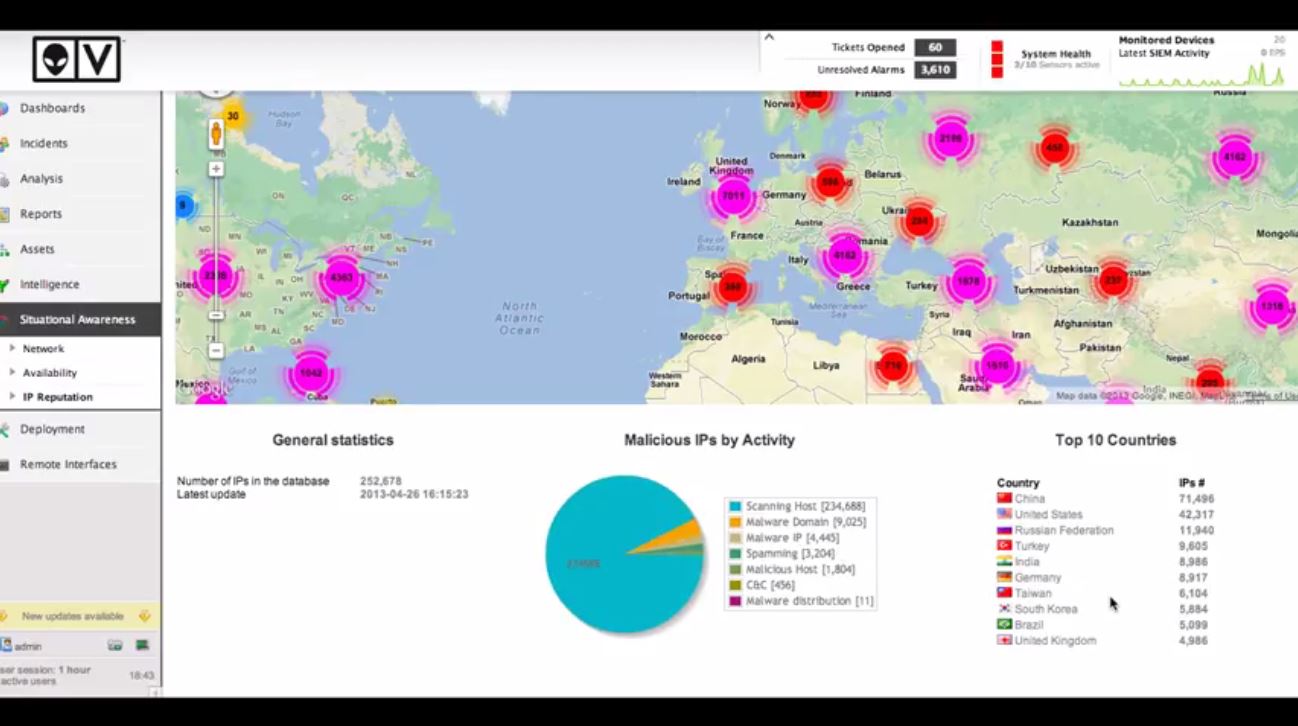
AlienVault Security Intelligence
Security analysts are like detectives. During security issues and investigations, they have to find the answer to the “who’s guilty?” as fast as possible. This can be complicated, especially if the mountain of data is constantly being generated. Context is key: a single piece of information may mean nothing, but it can become an important piece of a large puzzle.
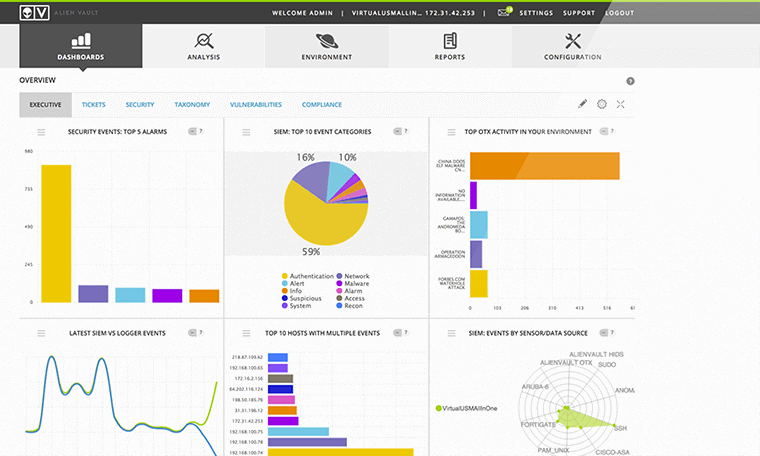
Security intelligence is an important part of solving this puzzle. With a series of real-time events using the built-in mandatory security feature, AlienVault’s Unified Security Manager platform provides a view to see all the pieces of the puzzle at a glance.
AlienVault Threat Management
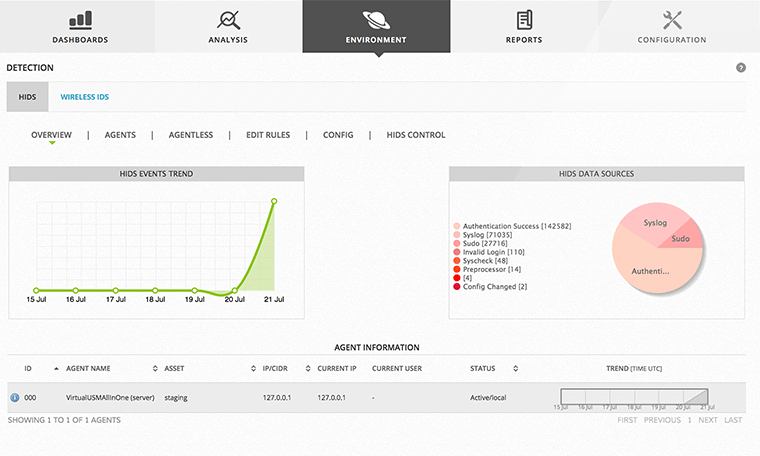
Today, organizations face a harsh reality with threat management. The global scene of risks is expanding rapidly, but safety budgets are only sparingly. When organizations recognize that they cannot completely cover the gaps with the budget they have, they must go beyond traditional methods and change their approach to security programs. Regular incident response helps organizations prepare for impending dangers, mitigate the impact when they occur, and bring a bitcoin-friendly refresh to their security programs.
Thanks to AlienVault USM’s threat manager:
AlienVault Vulnerability Management
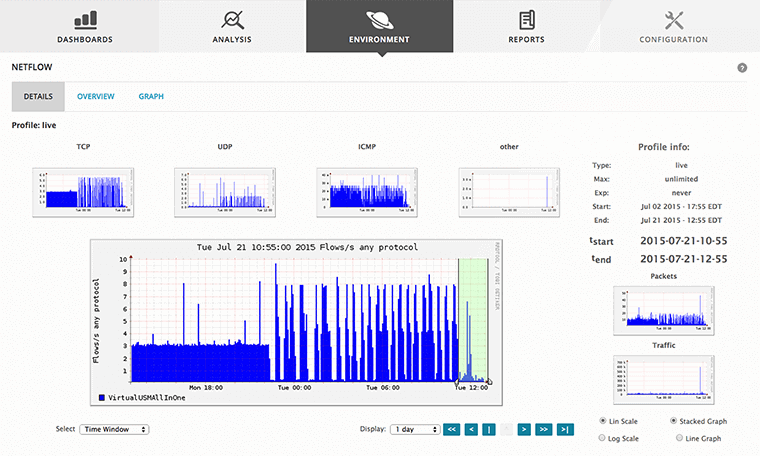
After identifying the vulnerabilities, remediation will be required. Remediation should be on the urgent to-do list, as thousands of vulnerabilities are discovered each year and seemingly endless security updates and patches are required. Vulnerability management is never “done”. Effective vulnerability management requires constant effort as new vulnerabilities are constantly discovered and organizations’ IT structures change over time.
With Vulnerability Manager: