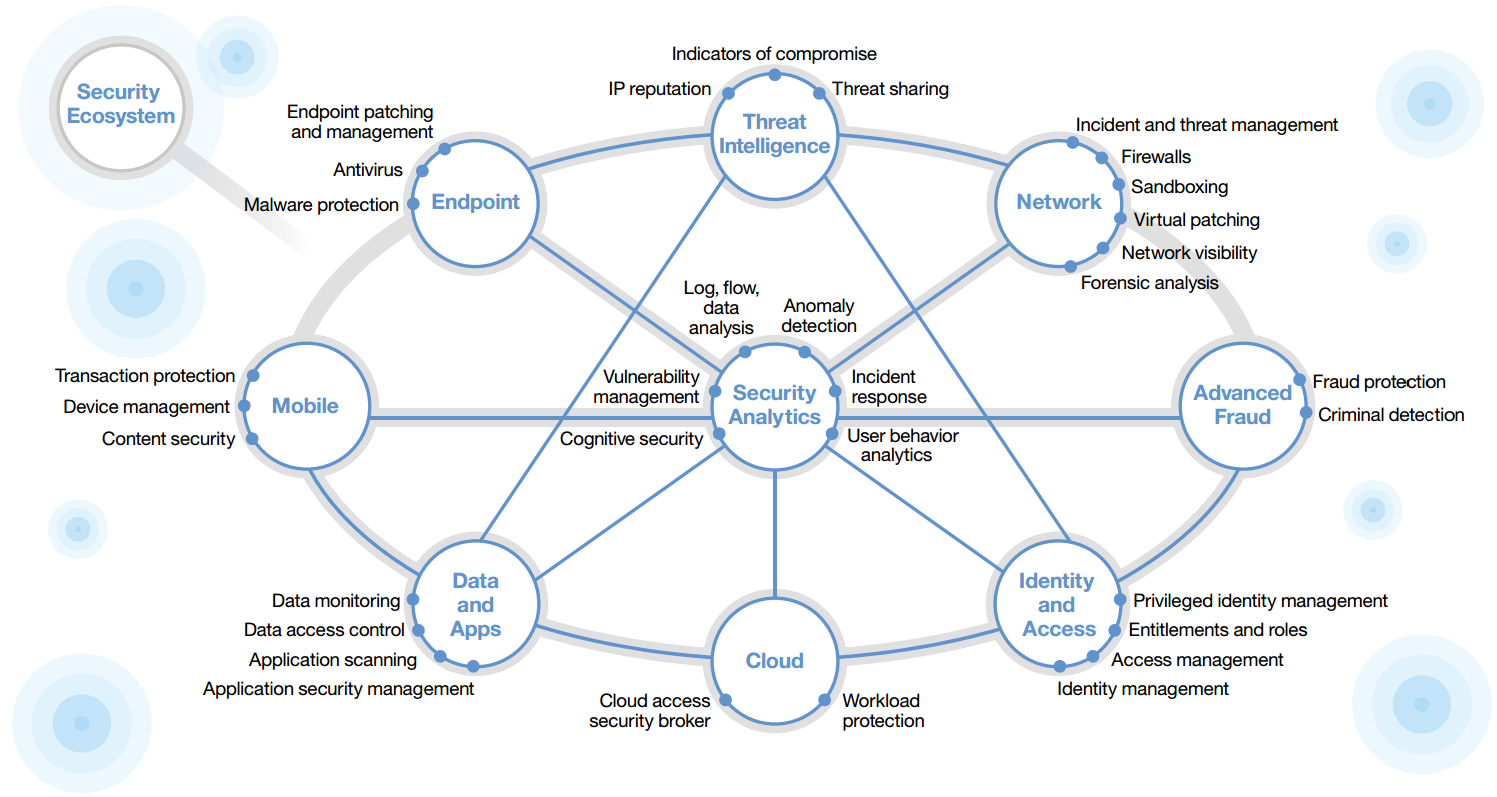
Protect critical data wherever it is located
IBM Security

IBM is the largest information technology company in the world. It operates in more than 170 countries with over 410,000 employees. IBM Security solutions is built on a framework that contains hardware, software, and services.
These capabilities consist of best practices and powerful tools that have been designed to provide:
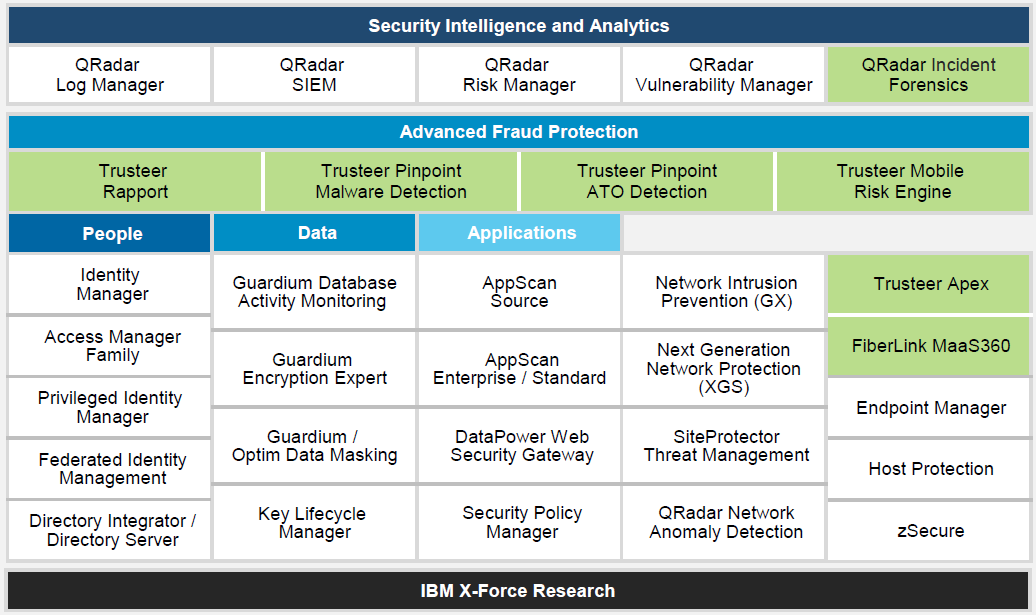
IBM Security Solutions Map
As cyber-attacks become more pervasive, it’s only a matter of time before your organization becomes a target. From the moment your security is compromised, every minute counts. IBM Security solutions help you identify, respond and block security breaches through integrated software and hardware solutions.
The powerful IBM portfolio of industry-leading tools provides unique security intelligence with less complexity and lower maintenance costs. IBM Security solutions helps you have a holistic and mature security posture that helps reducing costs, improving services, managing risks, and improving innovation.
Endpoint Protection
It means that you need to evaluate the vulnerabilities found in your enterprise network, speed up the risk prioritization process, and intervene in the threat in a matter of minutes at all endpoints. IBM Endpoint Protection solutions provide comprehensive endpoint security solutions to detect and stop advanced threats before they cause any damage.
IBM Endpoint Protection solutions help you:
IBM Endpoint Protection Solutions:
Network Protection
As you read this, attackers are constantly trying to hack into your network. They are using more and more sophisticated methods to find a way out. Do you have the visibility to stop them?
IBM Network Protection solutions are based on the time-tested security of the intrusion prevention portfolio. It provides new levels of security from advanced threats, enhanced network visibility, and progressive control between applications, users, and groups.
There will always be various attacks on your network, next generation network security solutions that recognize these attacks and adapt to block them in real time protect your infrastructure against these threats.
IBM Network Protection solutions help you:
IBM Network Protection Solutions:
Enterprise Mobility Management
Corporate mobility, which allows users to work effortlessly, collaborate frequently and attract customers, is very important for companies. IBM Enterprise Mobility Management combines device, application, and content management with powerful security to simplify your mobile device. You can monitor threats and automate compliance to maximize security without compromising user experience.
IBM Enterprise Mobility Management solutions help you:
IBM Enterprise Mobility Management Products :
Identity and Access Management
Today, organizations are required to manage and implement user access on multiple channels, including mobile, social, and cloud environments. These organizations also need to respond to business requirements, such as role management, compliance and audit reporting, and integrating different user groups. IBM Security identity and access management solutions help to strengthen compliance and reduce risks by ensuring the security of user access and monitoring user access in today’s environments which have multiple perimeter networks.
IBM Identity and Access Management solutions help you:
IBM Identity and Access Management Products :
Security Intelligence and Operation
Almost all security teams around the world demand to analyze and interpret billions of events per day for possible attacks that may happen. IBM Sense AnalyticsTM security intelligence can help you to identify and prioritize threats that pose the greatest risk to your business, so you can deal with them quickly. IBM’s intelligent approach to security helps you to find the threats quicker, identify the vulnerabilities, perform forensic analysis, manage the risks, automate compliance and respond to the incidents. IBM Security Intelligence and Operations solutions utilize security-related information across your organization, use analytics and automation to provide context and help you identify threats quicker, identify vulnerabilities, prioritize risks, perform forensic analysis, and automate compliance activities.
IBM Security Intelligence and Operations solutions help you:
IBM Security Intelligence and Operations Solutions :
Uygulama Güvenliği (Application Security)
IBM X-Force ® research constantly reveals that a significant part of the vulnerability is related to the use of web and mobile applications. In order to effectively overcome the security challenges of the application, organizations need to test their software and applications across their entire portfolio and reduce security costs; testing and verification should be done as early as possible. IBM’s industry-leading application security solutions help the organizations to minimize the risks while strengthening the compliance. Our team of security research experts can help your organization to create policies that will protect your system against attack threats and data breaches more effectively. It makes applications safe from malicious use today and helps you fix potential attacks in the future.
IBM Application Security solutions help you:
IBM Application Security Solutions :
Data Security
IBM Data Security solutions are a comprehensive data security platform that provides all capabilities from discovery and classification of sensitive data, to monitoring data and file activity, and masking, encryption, blocking, alerting and quarantine for the protection of sensitive data. Guardium helps to secure sensitive data in all environments, from databases to big data, cloud and file systems. Guardium also provides automated analysis to quickly uncover insider and outsider risks to sensitive data. The solution easily adapts to changes in your IT environment, whether it involves adding new users, requiring greater scalability, or adding new technologies.
IBM Data Security solutions help you:
IBM Data Security Solutions :
Advanced Fraud Protection
IBM Security Trusteer products, a holistic, integrated internet crimes fraud prevention platform, can detect and prevent online, mobile, and cross-channel fraud. Security Trusteer products helps you to prevent the true reason of fraud, reduces its operational impact, improves customer experience, and leverages global intelligence service. IBM Security Trusteer products help to detect and prevent hacking attempts of all kinds, which are responsible for the majority of online, mobile and cross-channel fraud. IBM Security Trusteer products provide a holistic and integrated cybercrime fraud prevention platform. This platform is based on four basic principles in order to help to prevent the root cause of fraud, improve the customer experience, reduce the impact on operations, and benefit from a global intelligence service.
IBM Anti-Fraud Advanced Protection Solutions :
Mainframe Security
IBM Mainframe Security solutions help you to protect your organization, detect threats, comply with policies and regulations, and reduce costs.
IBM Mainframe Security Solutions :
All IBM Security Products:
IBM Security Products Promotional Video
IBM BigFix
The Industry’s leading Endpoint Management Platform
BigFix is a powerful endpoint management solution widely used by organizations of various sizes to ensure endpoints are continuously patched, compliant and secure. For each endpoint, BigFix is able to collect a wealth of data including device attributes, patch status, deployment progress, etc. which is collected and stored centrally.
 FIND IT. FIX IT. SECURE IT… FAST- With BigFix Family
FIND IT. FIX IT. SECURE IT… FAST- With BigFix Family
You can further consolidate tools, reduce the number of endpoint agents, and lower your management costs by extending your investment in BigFix Compliance to include other modules in the BigFix family. It allows you to increase your control over with 3 capabilities:
1. BigFix Compliance, continuously enforces configuration compliance with thousands of out-of-the-box security checks aligned with industry-standard security benchmarks. Plus, it delivers advanced vulnerability posture reporting for remediation prioritization.
- Security Configuration Management, ensure continuous endpoint configuration compliance with effective remediation of configuration drifts. Supports security benchmarks published by CIS, DISA STIG, USGCB, and PCI DSS.
- Patch Management, deploy patches to distributed and virtual endpoints using Windows, UNIX, Linux and MacOS operating systems and third-party vendors, including Adobe, Mozilla, Apple, and Oracle – regardless of location, connection type or status.
- Device Discovery, Scan your entire network to identify all IP-addressable devices for pervasive visibility and control with minimal network impact.
- Compliance Analytics and Reporting, Collect, aggregate, and report on security configuration, patch and vulnerability compliance status of all endpoints against deployed policies. Track vulnerabilities, status and trends to identify security exposures and prioritize remediation.
2. BigFix Lifecycle, IT and Security Operations teams can quickly discover, secure, and manage hundreds of thousands of endpoints within hours or minutes. BigFix Lifecycle delivers the core “must have” endpoint management capabilities that these teams need daily. Lifecycle provides an automated, simplified, patch process that achieves greater than 98% first-pass patch success rates across Windows, UNIX, Linux, MacOS, AWS, Azure, VMware instances, located on and o the enterprise network. All automation and content streams are curated and tested, and once deployed, they are validated. Additionally, BigFix Lifecycle includes OS provisioning, software deployment, remote control, task sequence automation, and PC & Mac power management.
3. BigFix Inventory, This software enables users to discover and analyze applications installed on desktops, laptops, and servers. Drill-down information about software publishers, titles, and applications—down to the version level—also includes aggregated statistics and usage information. BigFix Inventory ddramatically reduce the time required to conduct a comprehensive software asset inventory for license reconciliation or compliance purposes. It provides valuable insight into what the organization owns—and what it has installed but does not own—along with how often the software is being used.
FIX More with Less Effort, with BigFix Modern Client Management.
- Most MDMs look the same; BigFix offers a single view for all your managed devices across all management methods.
- Dive deeper by viewing your co- managed devices alongside your classic devices.
- Combined with Insights BigFix Modern Client Management offers you more automation possibilities

Device Enrollment: Enroll devices via the browser with a link to the enrollment page
- Welcome email with link.
- End user supplies their corp credentials.
- Laptop enrolled in BigFix MCM, (optionally)
- BigFix traditional agent is pushed.
- Required corp software is installed, patches are updated, device compliance is established and maintained.
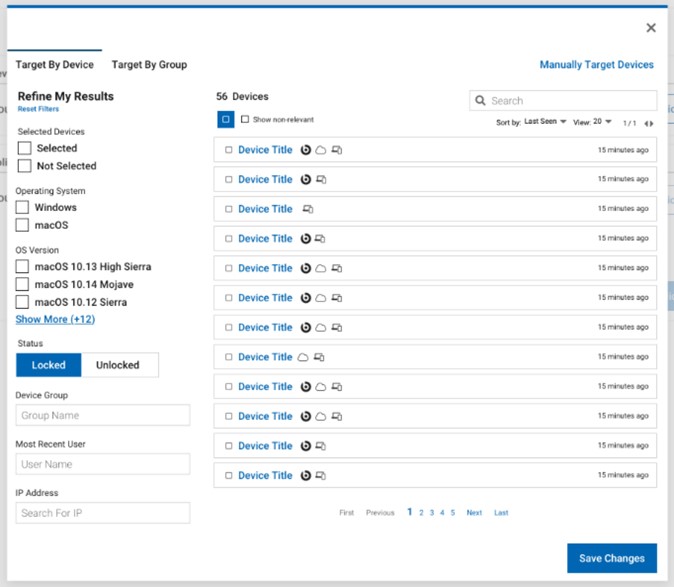
Device Inventory: Whether you’re working in the cloud or on-premises, get a single, comprehensive view of all your endpoints
- Represents Cloud endpoints
- Device managed with BigFix Modern
- Client Management
- Device managed with the traditional BigFix agent
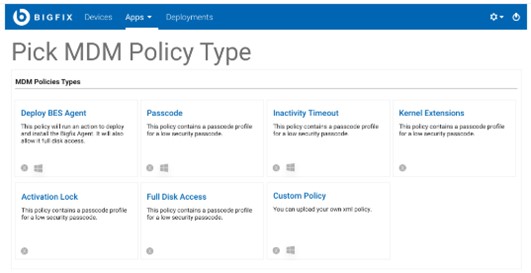
MDM Policies: You can create, edit, and manage MDM policies on modern endpoints
- Kernel Extensions
- Configuring Inactivity Timeout and Passcode settings
- OSX Activation Lock
- Configuring Full Disk Access for BigFix Traditional Agent

MDM Actions: You can deploy a set of actions to manage Modern Endpoints
- Lock Device
- Wipe Device
- Restart
- Shutdown
- Remove Policy
- Deploy the traditional BigFix Agent agents
BigFix is built on a unique, highly scalable infrastructure that distributes decision making out to the endpoints. This provides extraordinary functional and performance benefits across the entire BigFix family while reducing the cost of endpoint management and infrastructure complexity. BigFix features:
A single intelligent agent
The BigFix Agent performs multiple functions, including continuous self-assessment and policy enforcement, with minimal impact on system performance. The BigFix Agent initiates actions in an intelligent manner, sending messages upstream to the central management server and pulling patches, configurations, or other information, to the endpoint in real-time. The BigFix Agent runs on more than 90 operating systems across Microsoft Windows, Linux, UNIX, and MacOS.
BigFix Fixlets
BigFix Fixlets are small units of automation that allow IT Teams to simplify their daily operations and focus on more complex operations. BigFix provides more than 500,000 Fixlets out of the box. The BigFix team is continuously updating the Fixlet library, with over 130 content updates a month. BigFix users, business partners, and developers can leverage Fixlets to create custom policies and services for endpoints managed by BigFix. A community library of Fixlets is available on BigFix.me.
Highly scalable architecture.
A single BigFix Management Server can manage up to 250,000 physical and virtual computers, over private or public networks. Managed endpoints may include servers, desktops, roaming laptops, and specialized devices such as Point-Of-Sale (POS) devices, ATMs, and self-service kiosks.
Do More with Multicloud
Cloud endpoints can be easily discovered and viewed alongside traditional endpoints, in a single user interface, with BigFix 10. Knowing what you have is half the battle, and BigFix 10 allows you to go a step further and deploy the BigFix Agent for complete visibility, control, and security of these endpoints. It allows you to manage endpoints running in multiple cloud environments simultaneously – such as Amazon Web Services (AWS), Microsoft Azure, and VMWare – alongside physical and other on-premise endpoints.
BigFix minimizes the cost, time and efford required to discover, manage and secure endpoints in real-time
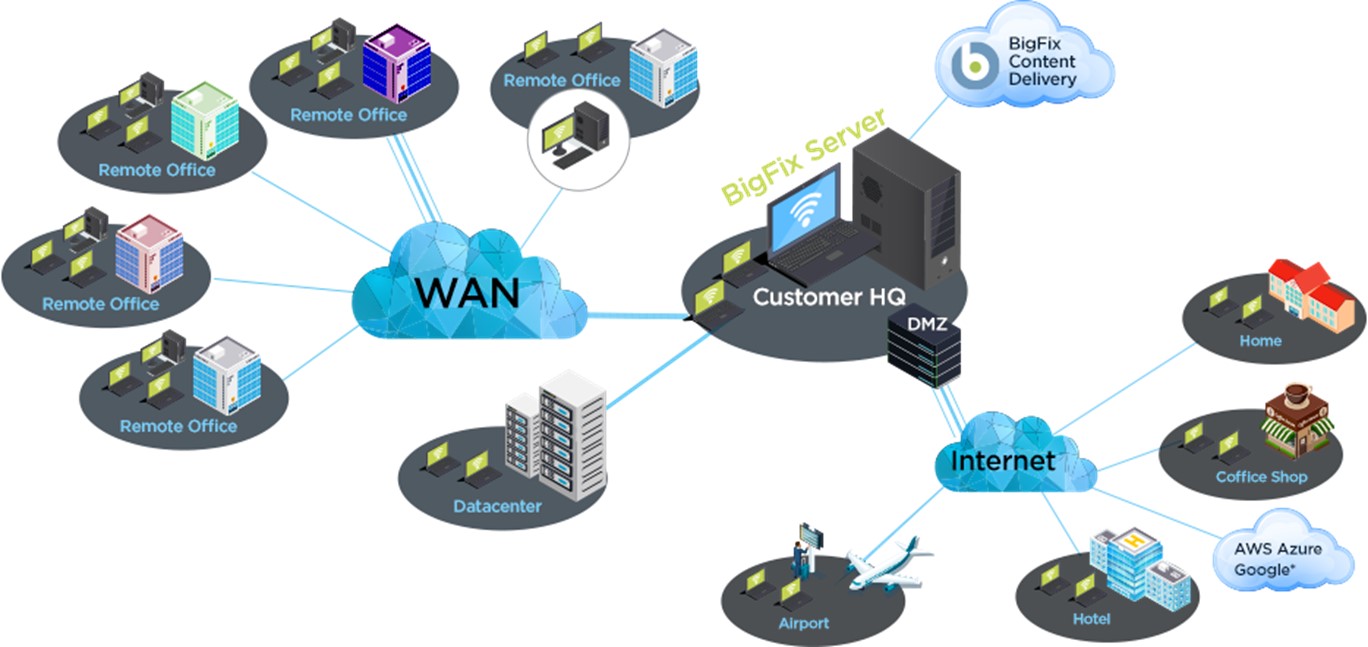
A single, comprehensive view of all your endpoints, whether they are running in the cloud or on premise
- Extend BigFix capabilities to the leading cloud providers: Amazon, Azure, Vmware
- Provide visibility and control for all your endpoints
- Simplify cloud visibility with native API support
- Automation to add the BigFix agent to perform patch, compliance, and inventory workflows
Quickly visualize risk while easily finding the endpoint issues that matter most
- A new analytic tools for deeper insight into risk and operational efficiency
- Powerful Data Repository to ingest data from all BigFix data sources
- Integrates data from leading vulnerability and incident response solutions worldwide
Out of the box reports
To demonstrate the benefits of all data consolidated to a single data repository and provide business value out of the box, BigFix Insights leverages Tableau Software® to provide four reports for several important endpoint management areas that many organizations constantly focus on: Patch Rhythm, Device Inventory, OS Migration, and Deployment Progress.
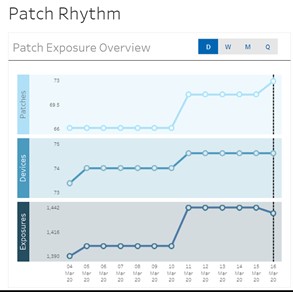
Patch Rhythm, Top down visuals that allow you to assess at-a-glance how well you are protecting the business
- Patch Rhythm addressing 4 key areas; Patch Exposure with timeline, Patch Exposure by Severity/Age, Exposures by Category, Exposures by Vendor
- High level and insightful data summaries, grouped by different criteria
- Quick drill-down to specific areas with filtering directly on the criteria
- Concise view of your exposure to vulnerabilities as a multiple of endpoints and applicable patches
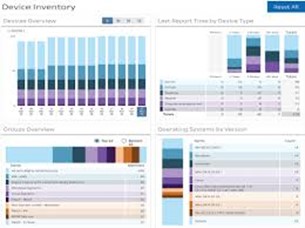
Device Inventory, Provide a view of all devices so that you can prioritize migrations from soon to be out of support operating systems
- Reports addressing 4 key areas; Device Overview, Last Report Time by Device Type, Groups Overview, OS by Version
- Device types by server vs workstation, hardware vs cloud/virtual, mobile vs stationary
- Drill down to level of detail desired/required
- Understand where your investment is regarding OS vendors
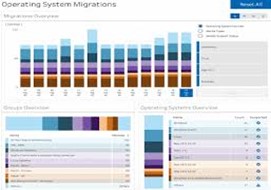
Operating System Migrations, Provide a clear view of OS migration efforts
- Reports addressing 3 key areas; OS Migrations, Groups Overview, OS Overview
- Clear understanding of the volume of effort to date and effort needed to complete migration
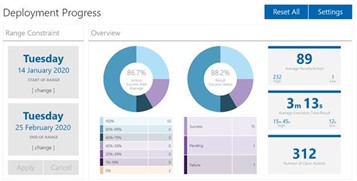
Deployment Progress, Provide a measure of success for patch or software upgrade efforts with an enterprise view for executives
- Addresses 4 key areas; Successful Deployment Over Time, Success Rate, By Group, Application Type
IBM XGS

IBM Security XGS Network Protection protects your infrastructure from advanced threats by providing new levels of security, enhanced network visibility, and progressive control across applications, users, groups.
The security vulnerability is reduced to advanced malware by increasing visibility and control over application and user behavior. It works with the latest data on internet threats to understand emerging threats in a shorter time and get more comprehensive insights and context.
Features of IBM Security XGS Network Protection:
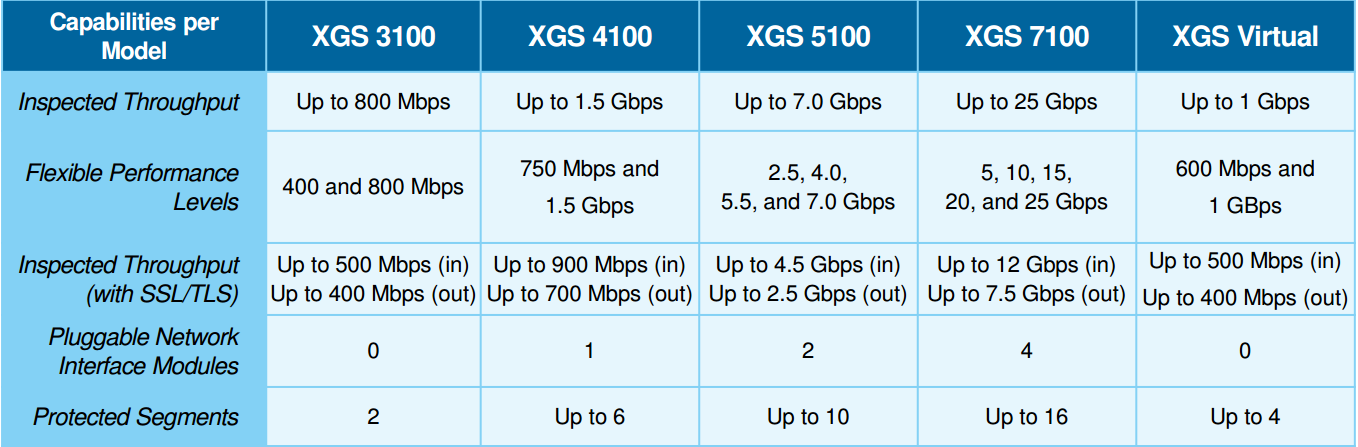
IBM Security Network Protection Model Comparison :
IBM Security Network Protection Video
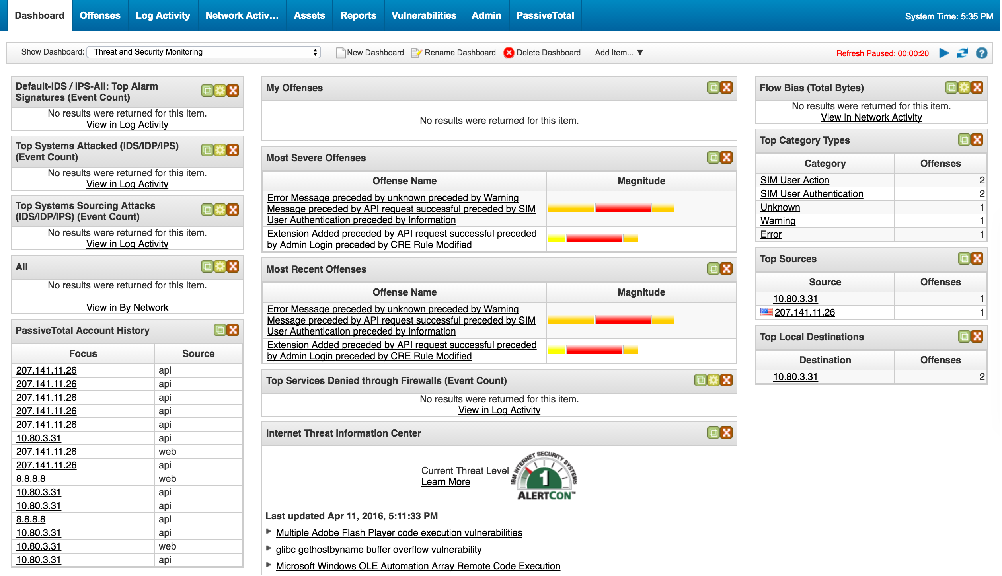
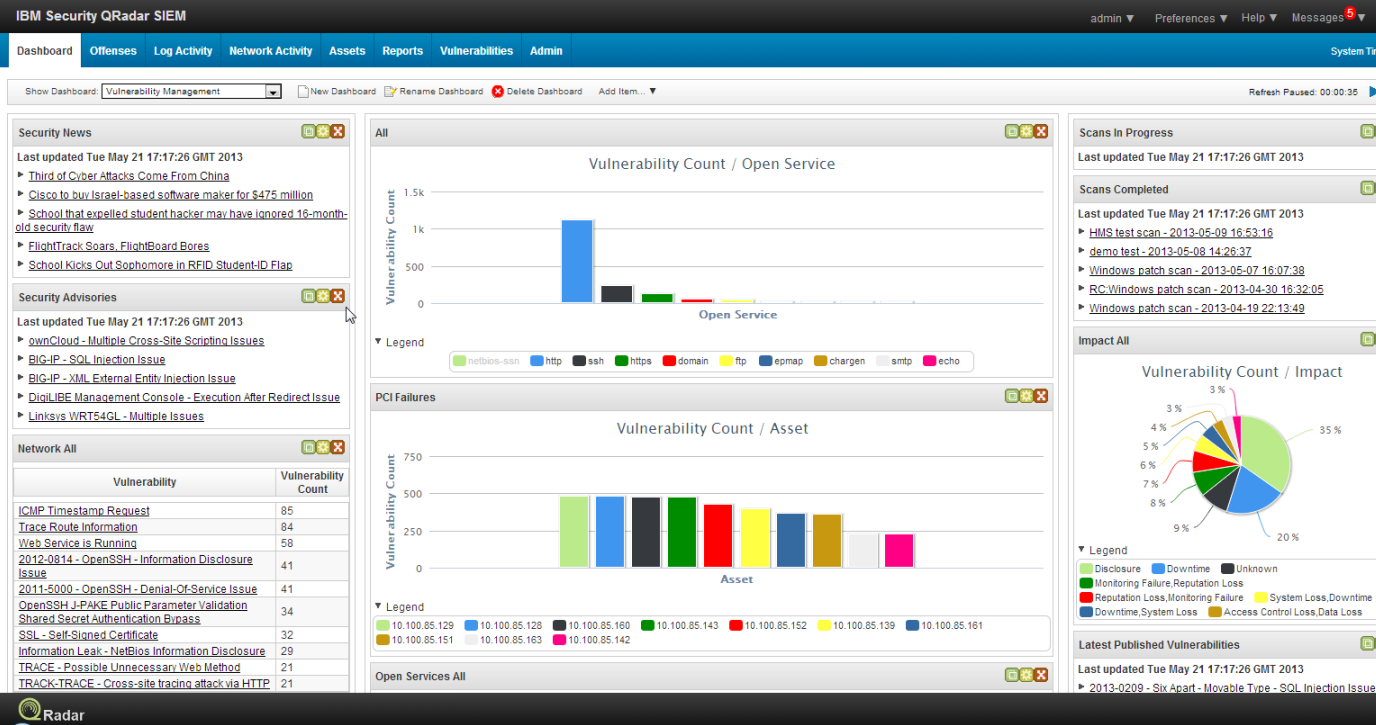
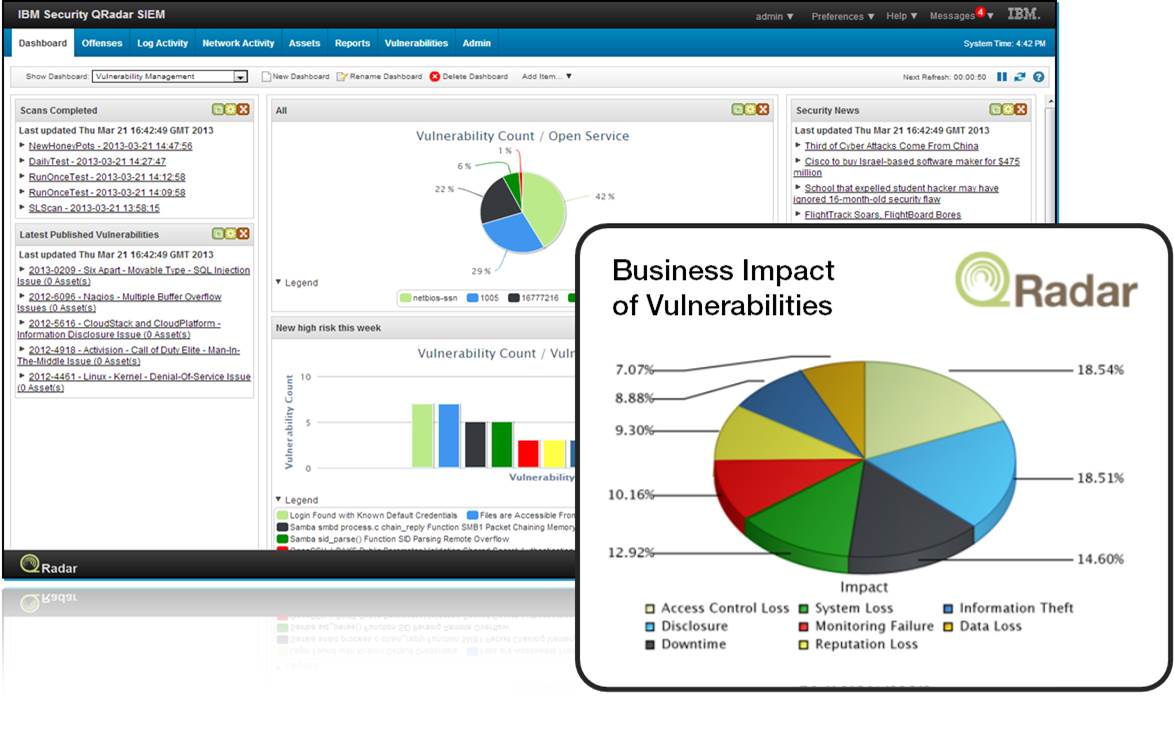
IBM QRadar
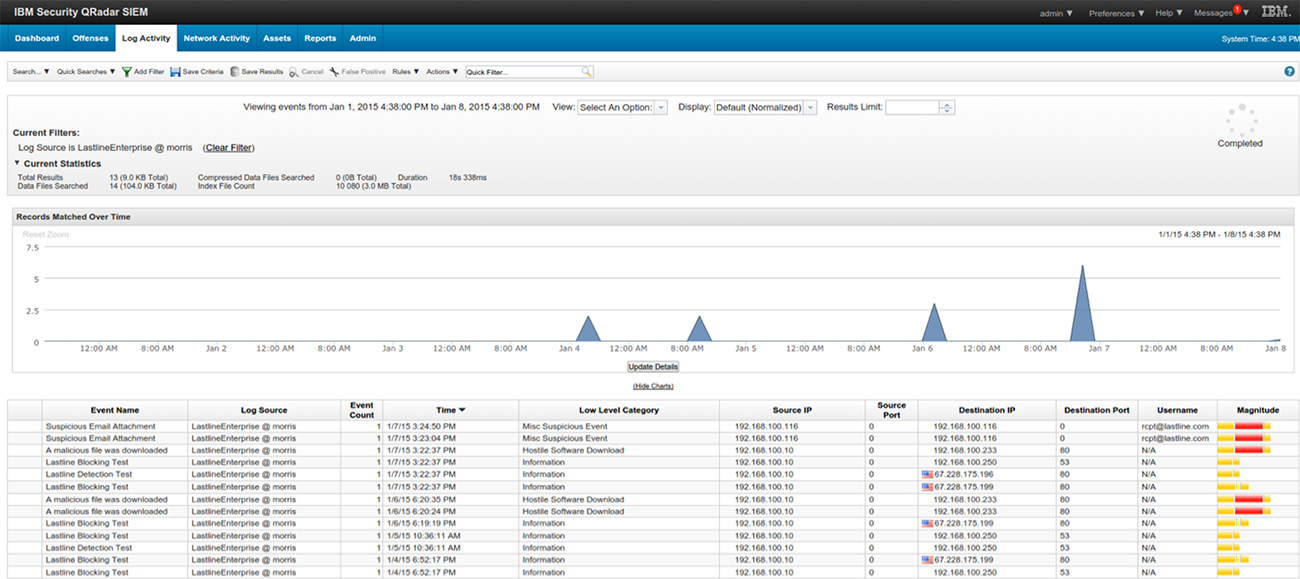
IBM QRadar SIEM combines log events and network flow data from thousands of devices, endpoints, and applications scattered across a network. IBM QRadar SIEM helps to prioritize security events by associating system vulnerabilities with event and network data.It normalizes and correlates the row data in order to detect the security errors, and it uses the advanced Sense Analytics engine to remove false positives, uncover advanced threats, detect anomalies, and ensure normal behavior. It includes the IBM X-Force Threat Intelligence software.
Features of IBM QRadar SIEM features:
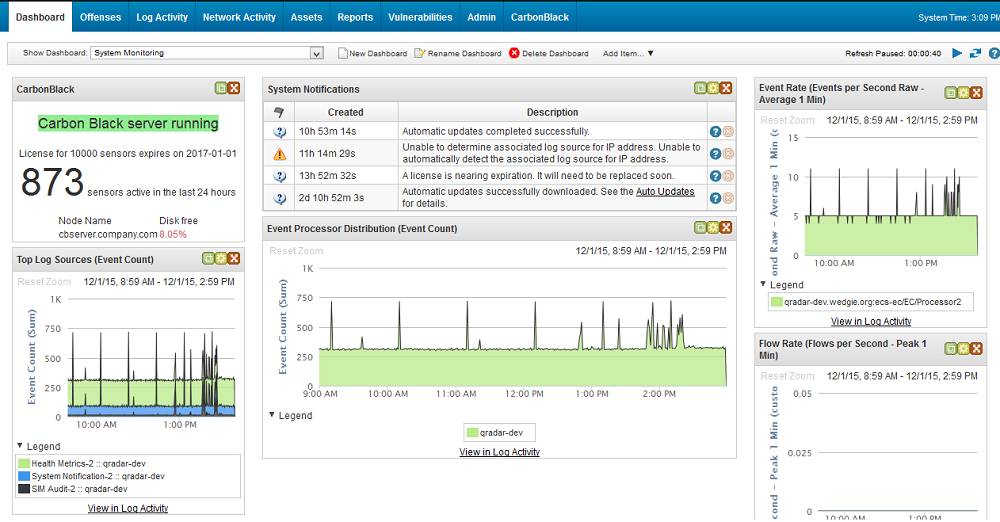
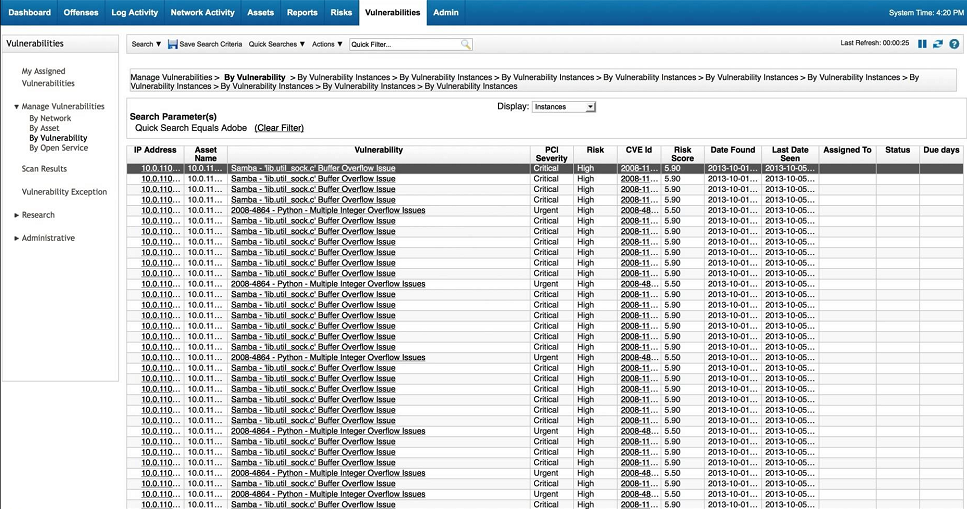
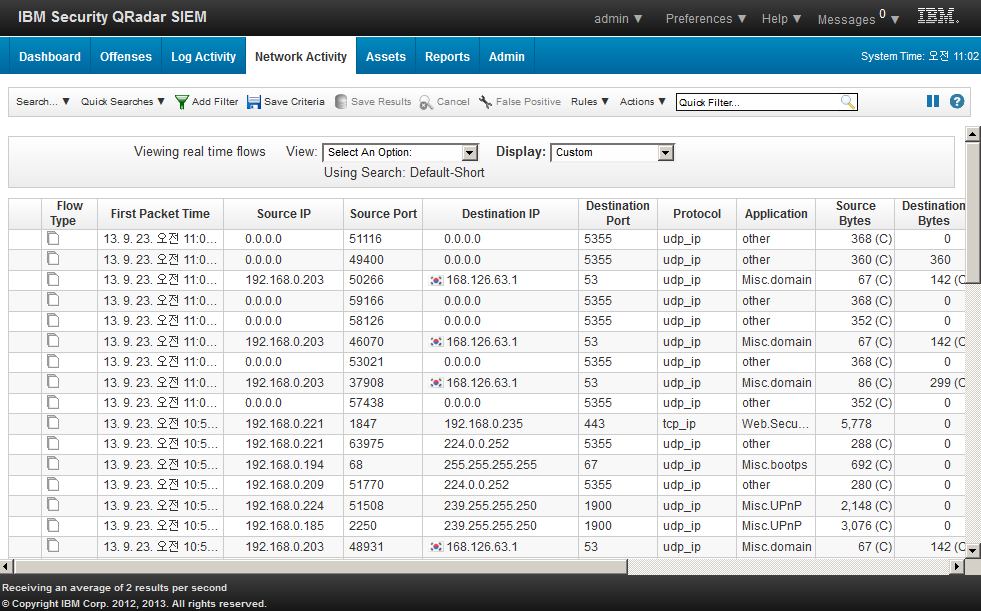
IBM QRadar SIEM Screenshots :
IBM QRadar SIEM Introduction Video
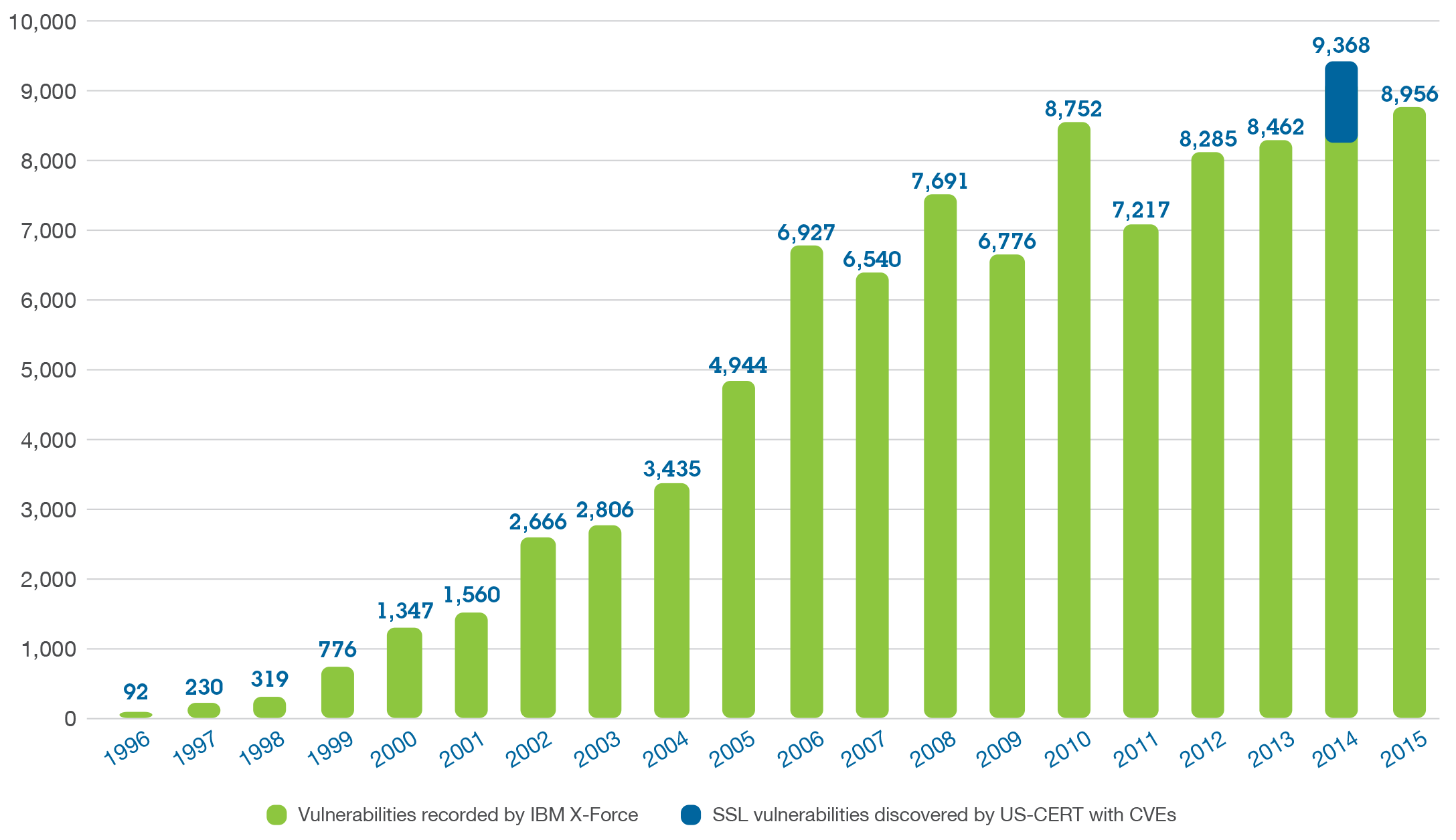
IBM X-Force
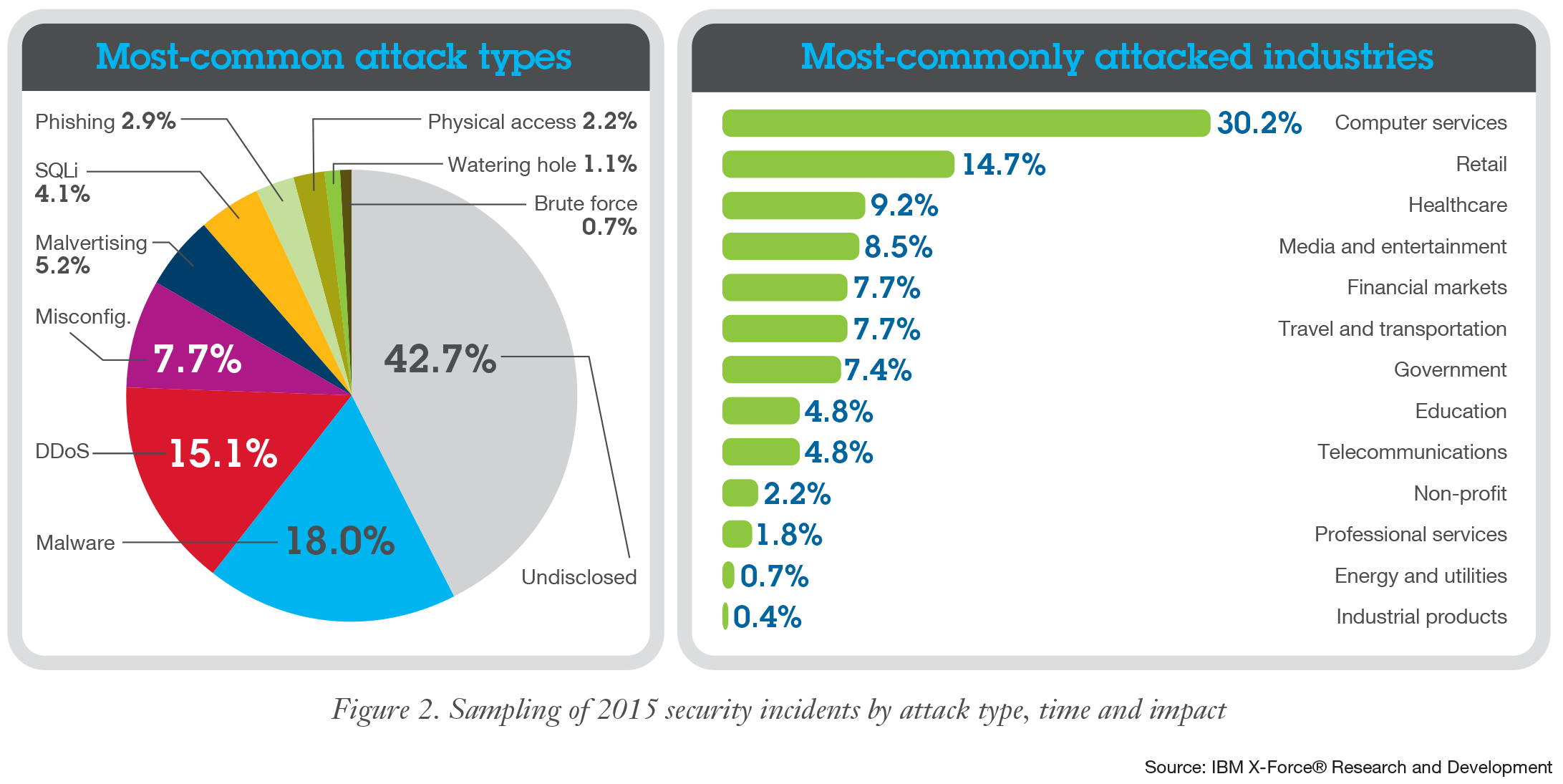
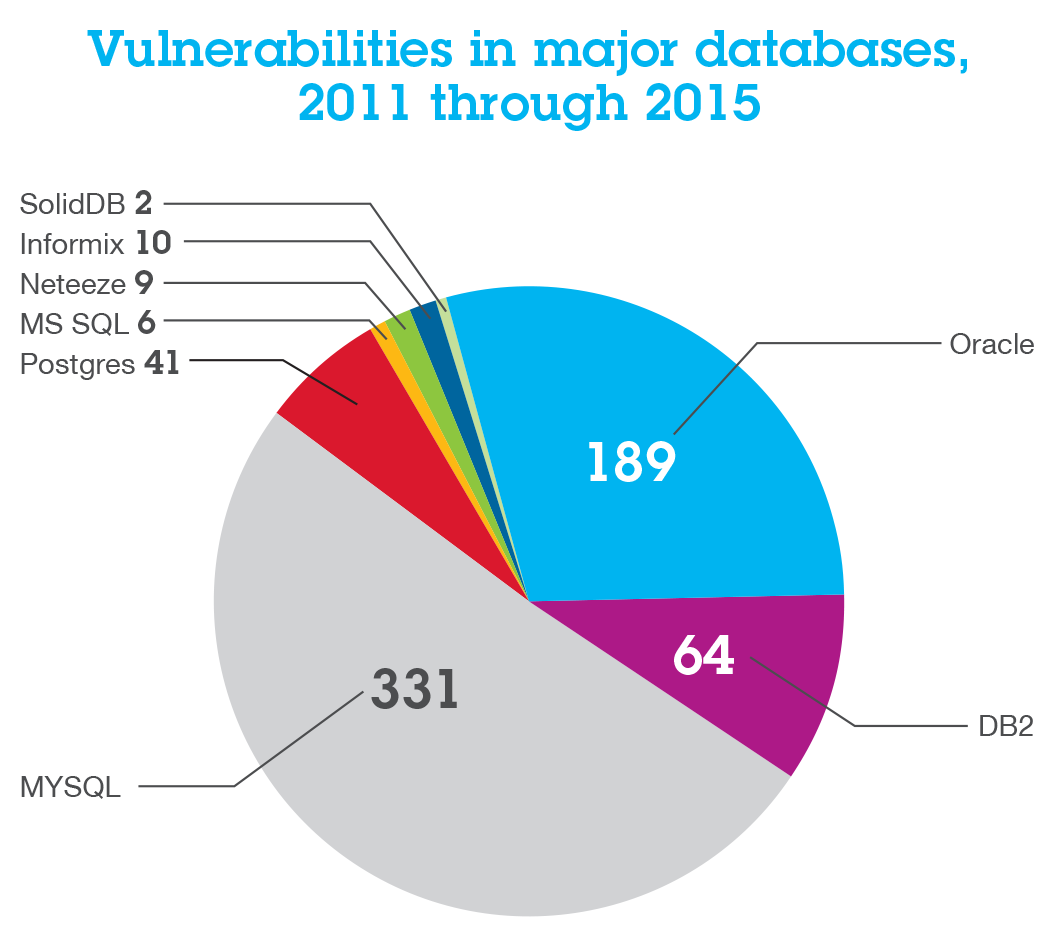
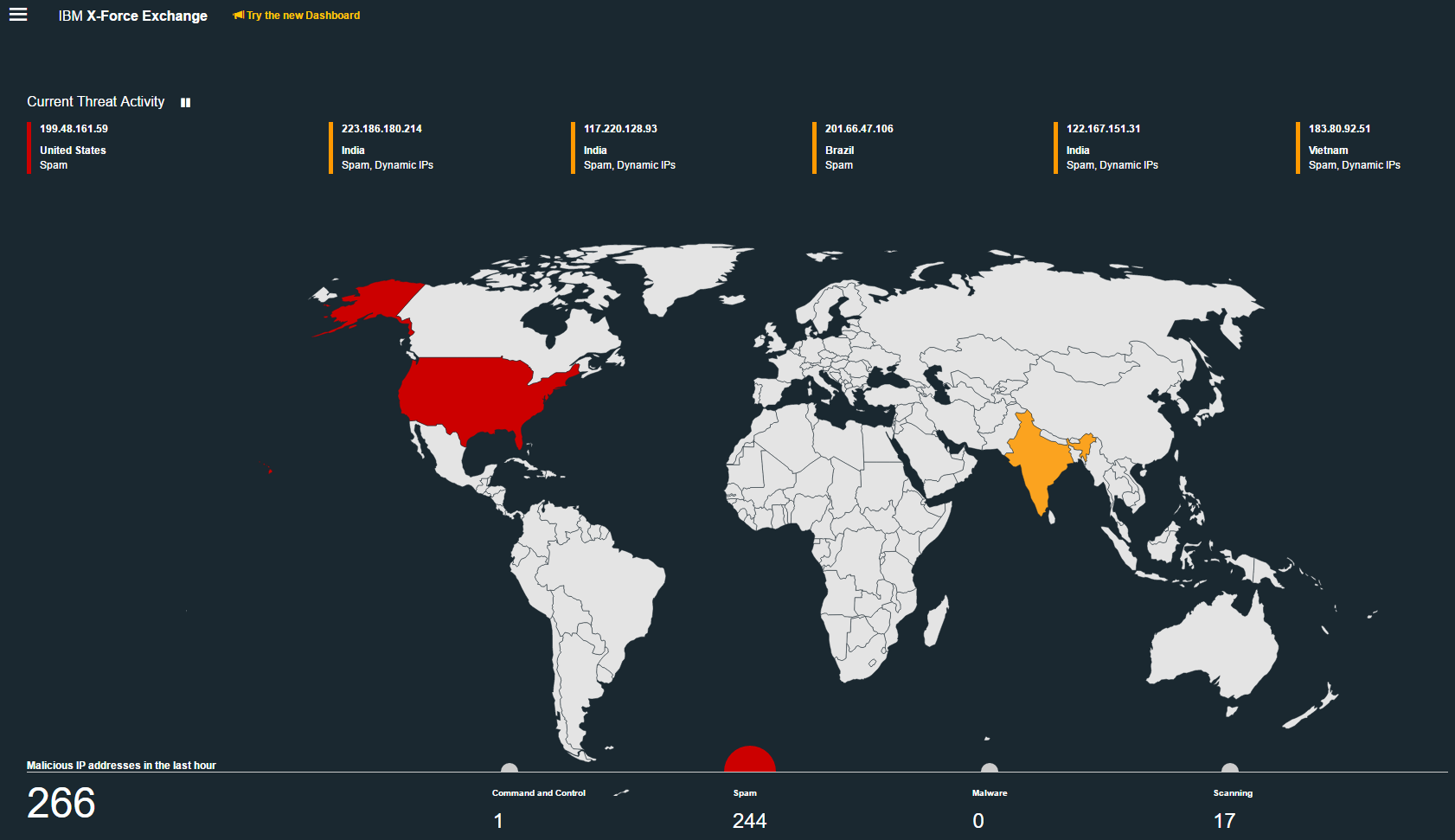
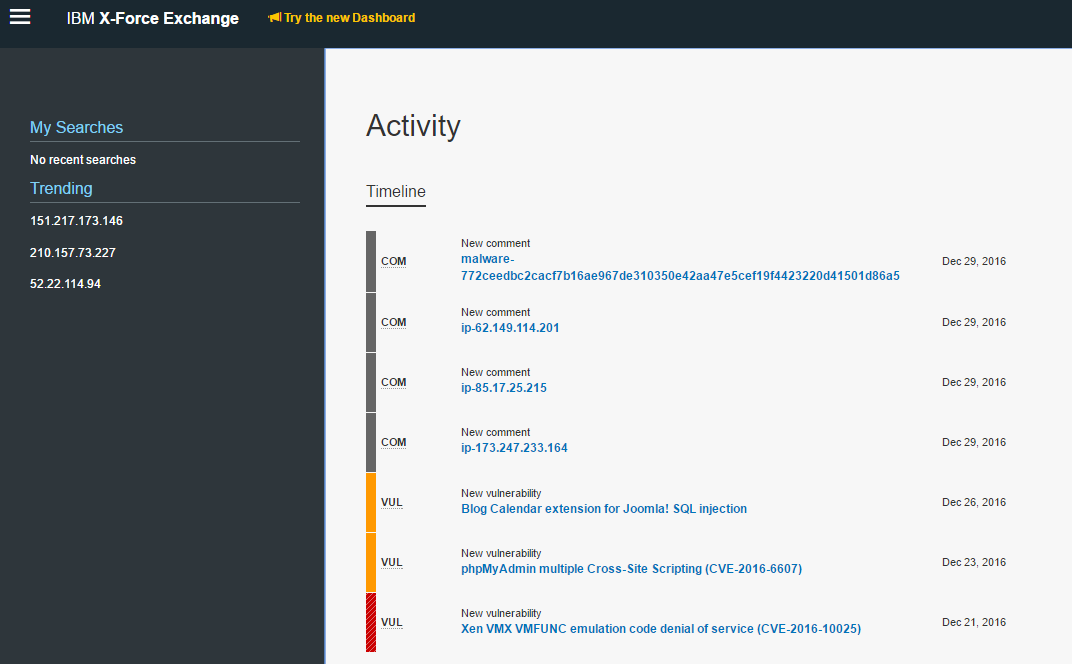
Security experts monitor and analyze security issues from a variety of sources, including a database of over 88,000 computer vulnerabilities, a web general information/document aggregator with over 25 billion web pages and URLs, an international spam compiler, and millions of spyware samples collected daily. IBM X-Force helps customers and researchers to have a better understanding of the latest security risks in general and overcome the emerging threats. It produces many thought leadership assets, including the IBM X-Force Threat Intelligence Quarterly Report. In addition, blog posts are regularly published on Security Intelligence.com, along with research papers and webinars based on the insights of our Managed Security Services.IBM X-Force Exchange is a cloud-based threat intelligence sharing platform that allows users to quickly research the most recent global security threats, gather responsive intelligence, and collaborate with peers. IBM X-Force Exchange is supported by human and machine-generated intelligence that utilises IBM X-Force scale.
The IBM X-Force Research and Development(R&D) team provides the foundation for a priority approach to Internet security. This group compiled from the security experts investigates and evaluates the vulnerabilities and security-related issues. It generates assessment and countermeasure technology for IBM products, as well as informs the public about new Internet threats. These insights are shared through blogs, documents, webinars, infographics, and interactive data visualizations.IBM Security X-Force Threat Intelligence enhances the IBM QRadar Security Intelligence Platform’s analytics capabilities by adding dynamic Internet threat data, for allowing you to gain more intelligence and choose the best security application. Enhancing the QRadar threat analysis capabilities with last-minute data on Internet threats helps organizations to see new threats faster, gain more insights and context, prioritize security events, and prevent or minimize attacks.
Features of IBM Security X-Force Threat Intelligence:
IBM X-Force Screenshots and Sample Reports:
IBM X-Force Introduction Video
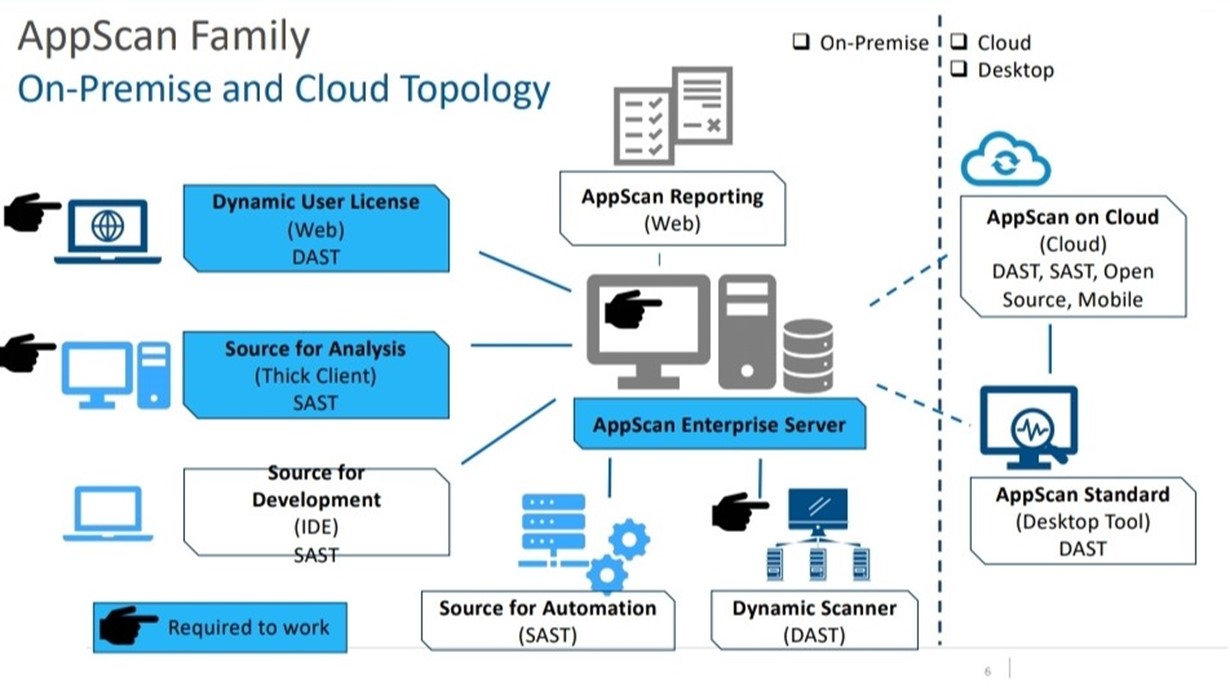
IBM AppScan
AppScan is a provider of application security testing tools that help software publishers detect and remediate vulnerabilities, and comply with regulations and security best practices. Its powerful static, dynamic and interactive scanning engines can deploy in every phase of the development lifecycle and test web applications, APIs and mobile applications. AppScan’s scanning engines are maintained by expert security researchers and continuously updated to remain current with new technologies and attack tactics.
- DevOps-ready application security testing that can work in harmony with most CI/CD pipelines
- Shift-left security to help businesses identify issues early in the development lifecycle, when they are easier and cheaper to fix
- A complete security testing suite that orchestrates multiple scanning technologies – DAST, SAST, SCA and IAST – to find more vulnerabilities
- Continuous vulnerability scanning to automate the testing of every incremental release and discover the vulnerabilities that can leave you open to risks
- Continuous compliance with regulations and industry best practices to ensure you are always in compliance
DAST (Dynamic application security Testing) VS SAST (Static application Security Testing)
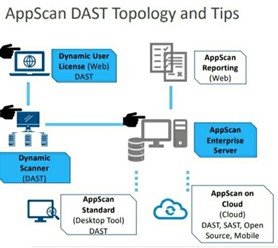
Dramatic acceleration of our DAST scans is enabled via a combination of new capabilities, including:
- Test optimizations focus on the more severe vulnerabilities, and those that are more likely to be identified, ensuring that shorter scans yield useful findings.
- Focusing scans on the significant vulnerabilities, and continuously adapting test policies to the current threat landscape, dramatically reduces scan times.
- In AppScan V10, users can choose to trade-o between speed (in some cases, up to 90% shorter test time) and depth or can still run full scans as needed.
- Incremental scans that focus only on the parts of the application that changed enable dramatic acceleration of scan times.
- Instead of analyzing the entire application for every release, scanners automatically identify those portions of the application that changed, and targets testing on that new functionality.
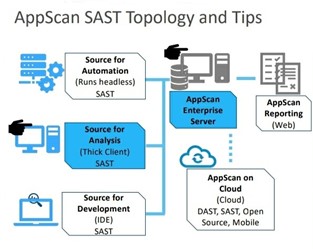
Faster SAST scans are enabled via three new capabilities introduced in our SAST scanning engine:
- Configurable scanning allowing operators to trade off speed for depth
- Distributed analytics used to accelerate computationally intensive processing by distributing it across multiple compute resources
- Incremental scans enabling shorter scans that focus only on parts of the code that changed
- More accurate scans are made possible using AI-based filtering and prioritization that focus attention on the high-severity vulnerabilities that require immediate attention.
Game-Changing IAST
AppScan V10 introduces an all new Interactive Application Security Testing solution that is easy to install, introduces a lower performance impact, and delivers better vulnerability detection. The IAST agent automatically instruments the application’s runtime and monitors for vulnerable code executions that require attention. More specifically, it monitors taint propagation and the quality of the application’s sanitizers.
AppScan IAST can be used in passive mode, without any deliberate eorts to exploit the application, or in active mode, where a DAST scanner is used to actively “attack” the application.
AppScan IAST can be used at any stage in the development lifecycle – IDE to production – to pinpoint vulnerable code executions for developers testing their code from the IDE, QA and security experts analyzing the application in a test environment, or operations teams monitoring the application in production.
Developer-Centric Testing Tools
AppScan V10 helps businesses implement shift-left security testing by introducing testing tools adapted for developer-use. AppScan’s IDE plug-in enables developers to run real-time scans on the code in the IDE. Vulnerable code is marked up – like a spellchecker would mark-up a misspelled word – and developers can easily fix the problem using contextual fix recommendations. AppScan also supports private SAST, DAST and IAST, to help developers identify problems in private, before they commit their code, and more importantly, before they impact the release cycle.
DevOps-Ready Automation
Improved APIs
AppScan V10 features dozens of new or improved APIs for triggering scans, modifying configurations, managing users, and more.
Improved plug-ins
The AppScan security testing suite features a rich set of plug-ins to ensure it works in harmony with other DevOps tools. V10 introduces major improvements to the Jenkins and UrbanCode plug-ins.
Cloud
AppScan on Cloud (ASoC) continues to deliver a comprehensive suite of security testing tools from the cloud, including SAST, DAST, IAST, SCA and mobile scanning. Customers can start scanning their applications without installing any software, and without any upfront license fees.
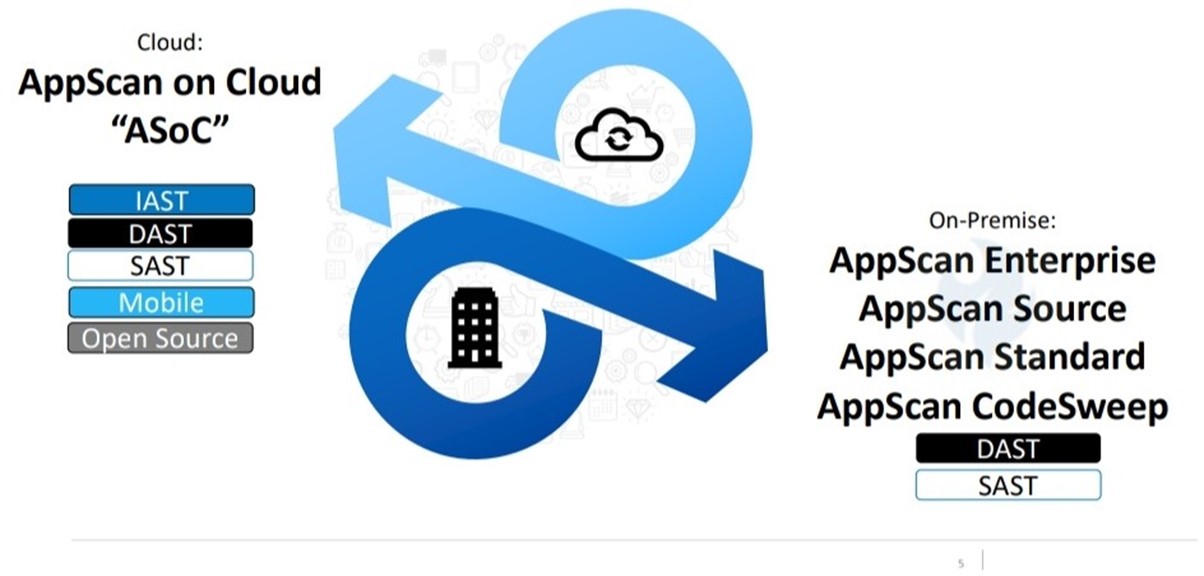
On-Premise
AppScan Standard is a dynamic application security testing tool designed for security experts and pen- testers. Using a powerful scanning engine, AppScan automatically crawls the target app and tests for vulnerabilities.
AppScan Enterprise delivers scalable application security testing and risk-management capabilities, to help enterprises manage risk and compliance. AppScan enables security, DevOps teams to collaborate, establish policies and perform testing throughout the application development lifecycle. AppScan Enterprise’s REST interface enables integration with various automation tools to ensure seamless integration with DevOps’ CI/CD pipelines.
AppScan Source helps organizations develop more secure software, and avoid costly vulnerabilities that surface late in the development lifecycle. By integrating security testing early in the development cycle – i.e. shift-left security – AppScan reduces risk exposure and reduces remediation costs.

IBM Guardium
IBM Security Guardium is a comprehensive data security platform that provides all capabilities from discovery and classification of sensitive data to monitoring data and file activity and masking, encryption, blocking, alerting and quarantine in order to protect sensitive data.
IBM Security Guardium helps customers to support all use cases, including compliance initiatives, privacy initiatives, big data security projects, and intrusion prediction projects, with comprehensive data protection.
IBM Security Guardium is designed to protect critical data wherever it is located. This comprehensive data protection platform enables security teams to automatically analyze what is happening in their data environment to help minimizing risks, protecting sensitive data from internal and external threats, and seamlessly adapting to changes that affect data security.
Features of IBM Security Guardium Product Family:
IBM Security Guardium Product Family
IBM Security Guardium Data Encryption
IBM Security Guardium Data Encryption provides encryption capabilities to help you protect structured and unstructured data and comply with the sector and regulation compliance requirements. This software performs encryption and decryption operations with minimal negative impact on performance and does not require any changes to databases, applications or networks.
IBM Security Guardium Data Encryption for DB2 and IMS Databases
IBM Security Guardium Data Encryption for IBM DB2 and IBM IMS™ Databases provides encryption for DB2 for IBM z/OS and IMS data systems. DB2 uses IBM System z encryption hardware to protect sensitive data at the line level and IMS segment level. It provides DB2 arrangement paths and IMS exit paths by using the z/OS Integrated Cryptographic Service Facility to protect sensitive data on storage media.
IBM Security Guardium Activity Monitor for Files
IBM Security Guardium Activity Monitor for Files can help you to meet compliance obligations and reduce the risks of large data breaches. IBM Security Guardium Activity Monitor for Files allows you to discover, monitor, and control access to sensitive files on local or networked file systems. It develops full visibility so that all processes on the file system, mounted and removable storage become visible for users, developers, outsourced personnel and applications.
IBM Security Guardium Data Privacy for Hadoop
IBM Security Guardium Data Privacy for Hadoop authenticates and monitors sensitive data in big data environments. The solution provides a number of Apache Hadoop capabilities to review or mask data, monitor and audit data activity, and protect common data definitions. IBM Security Guardium Data Privacy for Hadoop protects data in various Hadoop environments and supports compliance initiatives.
IBM Security Guardium Data Protection for Big Data
IBM Security Guardium data protection for Big Data Analytic provides cognitive analytics about sensitive data to explore unusual activities, prevents unauthorized data access, gives you alerts about any suspicious activity, automates compliance workflows, protects against internal and external threats. Continuous monitoring and real-time security policies protect data across the enterprise without negative performance impact or changes to data sources or applications.
IBM Security Guardium Data Protection for Databases
IBM Security Guardium data protection for databases provides cognitive analytic for efficient data tracking activities to detect unusual activities about the sensitive data, and it prevents unauthorized data access, gives you alerts about any suspicious activity, automates compliance workflows, protects against internal and external threats. IBM Security Guardium Data Protection for Big Data can be combined with IBM Security Guardium for Files for more comprehensive monitoring and protection of sensitive data across the enterprise.
IBM Security Guardium Data Protection for Files
IBM Security Guardium Data Protection for Files provides cognitive analytics for activity monitoring for sensitive data, to discover unusual activity related to sensitive data, it prevents unauthorized data access, alerts about suspicious activity, automates compliance workflows, and protects against internal and external threats. IBM Security Guardium Data Protection for Files helps you to meet compliance obligations and reduce the risks of large data breaches.
IBM Security Guardium Express Data Protection for Databases
IBM Security Guardium Express Activity Monitor for Databases provides you analysis, protection, and adoption capabilities to support data activity monitoring. It supports monitoring capability of efficient data activity for distributed database repositories. It provides a permitted, transparent and secure way to continuously monitor database activity, trigger preset real-time alerts about suspicious activity, and generate detailed audit logs for compliance reporting.
IBM Security Guardium Vulnerability Assessment
IBM Security Guardium Vulnerability Assessment specifies security risks such as missing patches, weak passwords, unauthorized changes, misconfigured privileges, and other vulnerabilities. IBM Security Guardium Vulnerability Assessment also detects behavioral vulnerabilities such as account sharing, unnecessary administrative logins, and unusual after-hours activity. IBM Security Guardium Vulnerability Assessments specify threats and vulnerabilities in databases that can be exploited by attackers and hackers to gain access to sensitive data.
IBM Security Guardium Data Redaction
IBM Security Guardium Data Redaction automatically specify sensitive content in unstructured data sources and protects sensitive data in documents, forms and files from inadvertent disclosure by detecting and removing data from the publicly shared document version. It supports many document formats such as scanned documents, PDF, TIFF, XML and Microsoft Word. On the one hand IBM Security Guardium Data Redaction supports data share for operational usage, on the other hand it is the fundamental component of information governance strategy which protects sensitive data.
IBM Security Key Lifecycle Manager
IBM Security Key Lifecycle Manager helps to meet the standards and regulations such as the Payment Card Industry Data Security Standard (PCI DSS), Sarbanes-Oxley, and the Health Insurance Portability and Accountability Act (HIPAA). It supports the OASIS Key Management Interoperability Protocol (KMIP) standard. It centralizes, facilitates and automates the encryption and key management process to help minimizing risks and reducing operational costs. It offers powerful key storage, service and lifecycle management for IBM and non-IBM storage devices.
IBM Security InfoSphere Optim Data Privacy
IBM InfoSphere Optim Data Privacy removes cookies from confidential information provided on demand, including big data platforms. It statically or dynamically masks data in applications, databases, and reports in production and non-production environments. InfoSphere Optim Data Privacy improves data protection and supports compliance initiatives. It masks confidential information in applications, databases, and reports based on business principles to protect data privacy.
Features of IBM Security Guardium Database Protection:
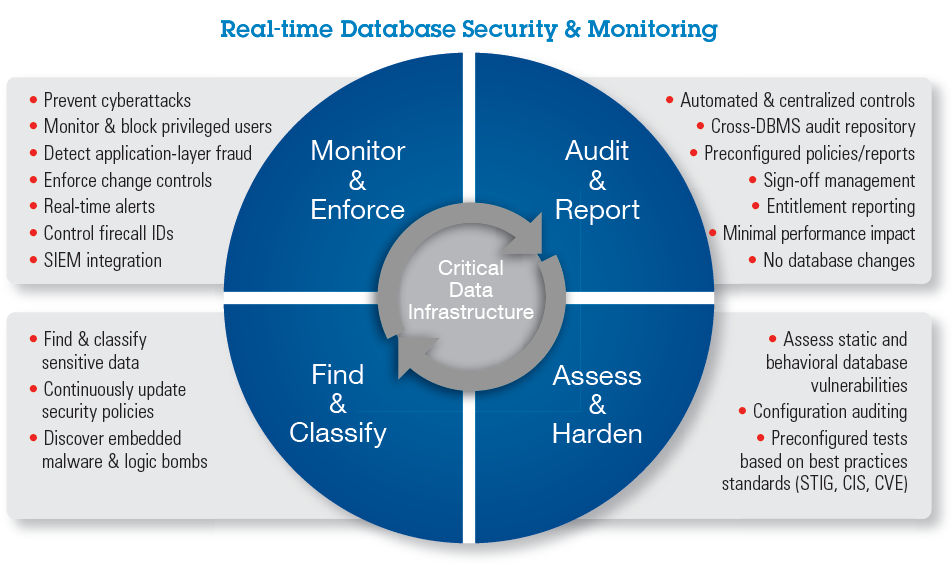
IBM Security Guardium Promotional Video:
IBM MaaS360
IBM MaaS360 is an organisational mobility management platform that can be deployed and scaled more easily. Companies can protect and centrally manage their mobile devices, applications, and content with IBM MaaS360, which offers flexible solutions to meet their specific needs. Many companies, from Fortune 500 companies to small and medium-sized businesses, rely on this software as the foundation of mobile initiatives that helps to provide mobile applications and content while protecting personal privacy and data security.
MaaS360 Product Family Versions
IBM MaaS360 Management Suite
It provides you an access to and control over the mobile devices and applications that your company uses. The software offers enterprise mobile device, application and expense management from a single screen; it allows you to authorize and manage policy settings, applications and data usage.
Features of IBM MaaS360 Management Suite:

IBM MaaS360 Productivity Suite
IBM MaaS360 Productivity Suite provides a solution to prevent loss of corporate data with consistent and seamless workflows for iOS, Android and other devices. It enables employees to securely access corporate data while protecting their mobile experience. Users can manage their email, calendar and contacts with an office productivity app which is independent and rich in terms of security. It aims to prevent loss of corporate data for mobile devices.
Features of IBM MaaS360 Productivity Suite:

IBM MaaS360 Content Suite
IBM MaaS360 Content Suite provides an easy and scalable way to distribute, manage and protect documents on smartphones and tablets. It allows employees to view, edit, and synchronize business documents across mobile devices while ensuring their manageability and control in an encrypted container that is rich in terms of security. Each document can have its own security policy and can be distributed to users, groups, or individual devices to create a highly personal and compatible user experience. It is an easy and scalable way to distribute, manage, and secure documents.
IBM MaaS360 Content Suite Features:
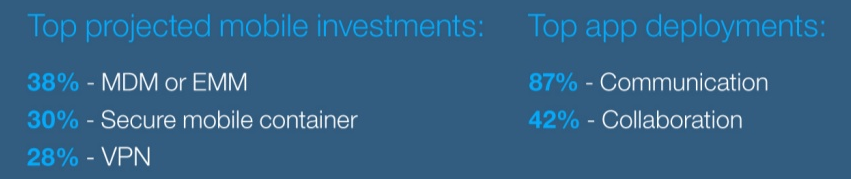
IBM MaaS360 Gateway Suite
IBM MaaS360 Gateway Suite provides products that provide mobile access to resources behind the firewall, such as SharePoint, Microsoft Windows file sharing content, intranet sites, and application data. It does not require any changes to your network, firewall security configuration, or device virtual private network (VPN) for access. IBM MaaS360 Gateway Suite helps to secure content by using the principles of authorization, encryption, and container approach.
Features of IBM MaaS360 Gateway Suite:

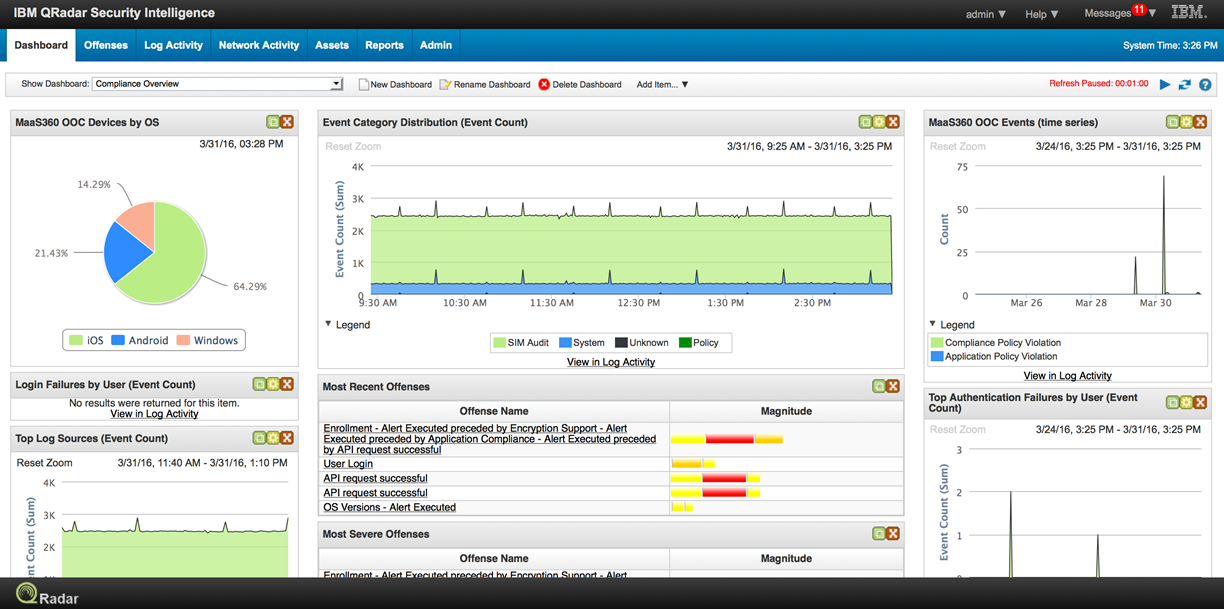
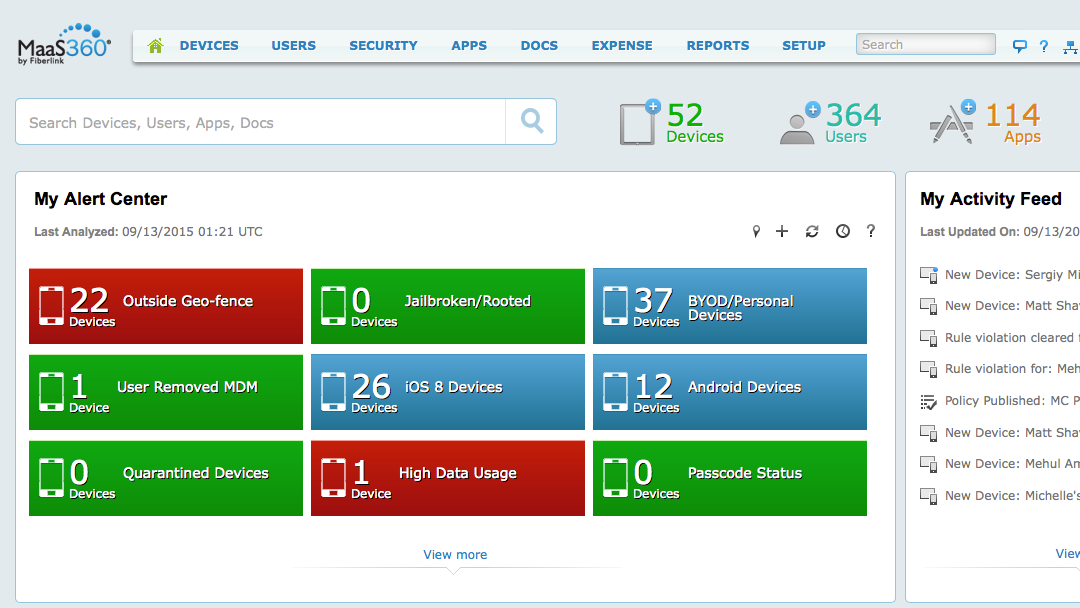
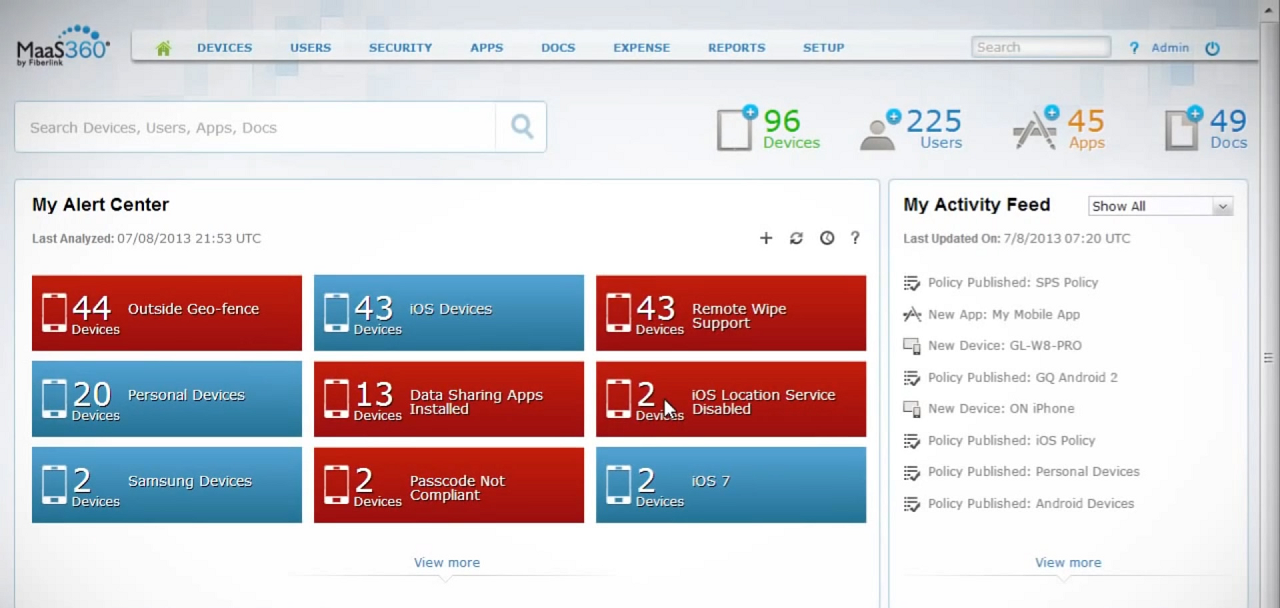
IBM MaaS360 Dashboard
IBM MaaS360 Demonstration Video